Author : MD TAREQ HASSAN | Updated : 2021/04/15
Azure Private Link
- Private Link provides private connectivity between applications deployed in virtual networks and Azure services using the Microsoft network
- Azure Private Link is a service from Azure that connects your Azure Virtual Network with Microsoft backbone network privately without exposing your service to the public internet
- Azure Private Link enables you to access Azure PaaS Services (i.e. Azure Storage, SQL Database etc.) and Azure hosted customer-owned/partner services over a private endpoint in your virtual network
- Traffic between your virtual network and the service travels the Microsoft backbone network. Exposing your service to the public internet is no longer necessary
- You can create your own private link service in your virtual network and deliver it to your customers
- The Private Link platform will handle the connectivity between the consumer and services over the Azure backbone network
- Azure Private Link has integration with Azure Monitor
See: Benefits of Azure Private Link
Azure Private Link is a secure and scalable way to create, share, and connect to Azure. All data that flows from a provider to a consumer is isolated from the internet and stays on the Microsoft back end.
- Consumers: To privately connect to a service, create a private endpoint
- Providers: To privately render a service, create a private link service or private resource
Notes:
- To use private link with Azure resource (i.e. WebApp), that resource has to met a minimun pricing tier (SKU)
- There is no Azure resource named “Private Link”, rather you go to Private Link Center (see below) and can do followings
- Can create Private Endpoint for connecting your service to PaaS in Microsoft backbone network
- Can create Private Link Service to allow others to access your Azure resource via private link
- Private Link is not a free service
Private Endpoint
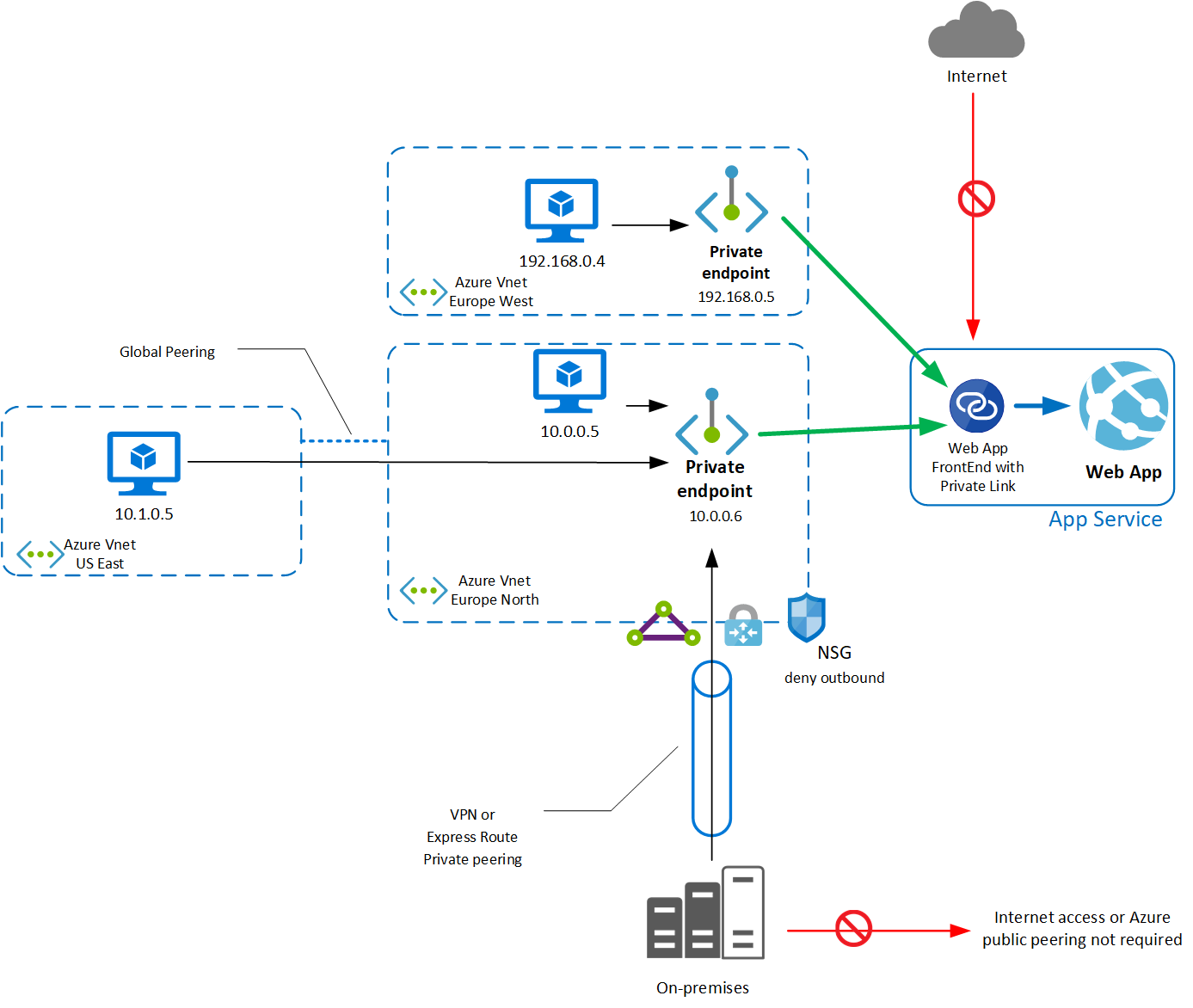
- Azure Private Endpoint is a network interface(NIC) that connects you privately and securely to a service powered by Azure Private Link
- A private endpoint is a special network interface for an Azure service in your Virtual Network (VNet). When you create a private endpoint for your Azure PaaS resource (or third party Azure resource), it provides secure connectivity between clients on your VNet and your Azure PaaS resource
- You can use private endpoints to allow ingress of events directly from your virtual network to Azure resource securely over a private link without going through the public internet
- Private Endpoint uses a private IP address from your VNet, effectively bringing the service into your VNet (in other words, private endpoint brings other service into your vNet using private link)
- The network interface associated with the private endpoint contains the complete set of information required to configure your DNS, including FQDN and private IP addresses allocated for a given private link resource
- Private Endpoint is create in Private Link Center
- Private Endpoint is created in a subnet of your vNet and if NSG is applied to that subnet then NSG for Private Endpoint will be disabled but other resources in that subnet will still be subjected to subnet NSG
[Image courtesy: Microsoft Doc.]
Notes:
- A private Endpoint is created in your vNet for a target resource, and traffic (from your vNet) goes to that target resource via “PrivateEndpoint@PrivateLink”
- private Endpoint provides secure connectivity between clients on your virtual network and target Azure resource
- In context of Private Link, a Private Endpoint acts as entry point to target service which means Private Endpoint only deals with Inbound traffic to the target service from your vNet (not outbound traffic from target service to your vNet)
- If you add Private Endpoint to a Azure resource i.e. App Service
- Inbound traffic may come to App Service through Private Link
- Outbound traffic from App Service will still go through public internet (to strict outbound traffic use “vNet integration” fetaure or other Azure service)
Limitations of Private Endpoint:
- The IP address of the Private Endpoint NIC must be dynamic, but will remain the same until you delete the Private Endpoint
- The NIC of the Private Endpoint cannot have an NSG associated.
- User Defined Routes do not apply to Private Endpoint
More:
Private Link Center
- A seperate portal inside Azure portal
- Similar to Universal Print Portal
- Left panel tabs:
- Private endpoints: managing private endpoints
- Private link services: Creating private link service so that others can access your Azure resources (allowing others to access your resources using private link)
- Pending connections: Actions on pending connections (to your resources) from others over private link
- When you try to create Private Link in Azure portal, it will redirect you to Private Link Center (Create private link: https://portal.azure.com/#create/Microsoft.PrivateLink-ARM)
- In Azure portal home page, you can search “private link” and it will redirect you to Private Link Center: https://portal.azure.com/#blade/Microsoft_Azure_Network/PrivateLinkCenterBlade/overview
Private Link Service
- Azure Private Link service is the way you allow your Azure resource (or service) to others (consumers) over Azure Private Link
- Your service that is running behind Azure Standard Load Balancer can be enabled for Private Link access so that consumers to your service can access it privately from their own VNets
- Your customers can create a private endpoint inside their VNet and map it to this service
- Details: https://docs.microsoft.com/en-us/azure/private-link/private-link-service-overview
For PaaS services i.e. Azure storage account, Private Link Service is eanbled and therefore all you need to do to allow access vNet to storage account:
- Enable RBAC for Azure resources from Azure AD if not enabled
- Create Private Endpoint in Private Link Center
Service Endpoint
- VNet service endpoint provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network
- Service Endpoints allow you to secure your critical Azure service resources to only your virtual networks
- Service Endpoints enables private IP addresses in the VNet to reach the endpoint of an Azure service without needing a public IP address on the VNet
- When Service Endpoint is used:
- Traffic flows fron your vNet to the service resource over the Azure backbone network instead of over the internet
- You can strict the target resource in such a way that it only accepts traffic from the subnet of your vNet that is associated with the service endpoint
- Service Endpoint is a subnet level setting and it connects to public endpoint (i.e. public IP) of the target service
Use case:
A virtual machine (VM) in a VNet that needs to communicate with an Azure storage account.
You can combine a service endpoint, storage account, and NSG so that traffic from a VM in a private subnet reaches
the storage account without hitting the internet, the storage account blocks all traffic unless it's from that subnet,
and the NSG restricts outbound traffic from the subnet to the internet.
Why to use Service Endpoint in the above use case?
- Without Service Endpoint, the traffic has to go through public internet
- In order to traffic to go through public internet, public IP address needes to be assigned to VM and storage account has to allow traffic from “all networks”
- Both “public IP address of VM” and “allows traffic from all networks for Storage Account” are security concerns
- To avoid these security concerns, Service Endpoint can be used
Example: creating Service Endpoint for storage account
- Configuration on vNet side:
- When you add subnet to vNet, there is a section “SERVICE ENDPOINTS” where you can add Service Endpoint for specific service (in this case
Microsoft.Storage) - Existing Subnet: go to vNet > Settings: Subnets > “SERVICE ENDPOINTS” add service endpoint (
Microsoft.Storage) for storage account
- When you add subnet to vNet, there is a section “SERVICE ENDPOINTS” where you can add Service Endpoint for specific service (in this case
- Configuration on Storage Account side:
- Storage Account > Settings: Networking > Firewalls and virtual networks > Allow access from: Selected networks
- Add subnets in which you created service endpoint
Notes:
- All resources in the subnet (in which service endpoint is added) would have unrestricted access to the target service
- To strict access to ther target service, use Service Endpoint Policy
- Service endpoint policy
Service Endpoint vs Private Link
- Similarities:
- Both are created in your virtual network, allowing a client (consumer) living in your vNet to access to a PaaS service that is outside of your vNet
- Both promote network security by allowing VNet traffic to communicate with service resources without going over the internet
- In both cases traffic goes through Microsoft backbone network instead of internet
- Differences:
- Private link costs money, but there is no cost for service endpoints
- Service endpoints do not support on-premises traffic, private endpoints support traffic from on-premises via ExpressRoute, private peering, and VPN tunnels
- Public vs. private destination IP address:
- Service Endpoint: vNet private IP -> target service public endpoint
- Private Link: vNet private IP -> target service private IP (essentially target service is into the network mentioned that Private Enpoint would have private IP address from subnet and that subnet belongs to your vNet)
- Creation:
- Create and manage in Private Link Center (dedicated protal)
- Create and manages in “vNet > Settings: Subnets > Service Enpoints” (+ allowing only that subnet in targer resource networking settings)
- Read (good article): https://www.fugue.co/blog/cloud-network-security-101-azure-service-endpoints-vs.-private-endpoints
Service Tag
- A service tag represents a group of “IP address prefixes” from a given Azure service
- Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules
- Service tags are used in place of specific IP addresses when you create security rules
- By specifying the service tag name, such as ApiManagement, in the appropriate source or destination field of a rule, you can allow or deny the traffic for the corresponding service
- You can use service tags to define network access controls on network security groups or Azure Firewall
- See: Available service tags
Example: block internet access and allow storage account access using NSG rules (2 rules) with service tag for a VM
Source: VirtualNetwork
Destination: Service Tag
Destination service tag: Storage
Destination port ranges: * (asterisk)
Action: Allow
Priority: 100
Source: VirtualNetwork
Destination: Service Tag
Destination service tag: Internet
Destination port ranges: * (asterisk)
Action: Deny
Priority: 110
VNet Integration
- Puts a PaaS service into your VNet
- See: App Service Virtual Network Integration
Note: Some services are natively deployed within a Virtual Network, so there’s no need for VNet Integration or private endpoints
Subnet Delegation
- Subnet delegation enables you to designate a specific subnet for an Azure PaaS service of your choice that needs to be injected into your virtual network
- Subnet delegation provides full control to the customer on managing the integration of Azure services into their virtual networks
- You can not add your resources into delegated subnet
- Example: SQL Server Managed Instance uses delegated subnet and by default can be accessed from your vNet only (public access disabled by default)
Private Endpoint vs vNet Integration
- Private Endpoint: Your vNet -> target service for which Private Endpoint (@private link) is created
- vNet Integration: Target service -> your vNet (by default, vNet Integration does not strict all traffic to vNet only, outbound traffic from that target service can still go to public internet. But you can strict all traffic to vNet only by settings/configurations)
Security Hierarchy
Subnet delegation: puts PaaS service into my VNet (i.e. SQL Server Managed Instance)
Private Endpoint (Private Link): vNet private IP -> PaaS service private IP
Service Endpoint: vNet private IP -> PaaS service public IP
Managed Identity
Securely Access Azure SQL Database
- Use one of the followings
- Firewall settings
- Deny public access: No
- Allow Azure services: No
- Use Service Endpoint on vNet subnet (i.e. AKS cluster subnet)
- Add vNet subnet as white listed subnet in Virtual networks section
- Endpoint (Private Link)
- Firewall settings
- Use Managed Identity to acess Azure KeyVault and get connection string
- Access Database using connection string